Securing the Future: Exploring the Cybersecurity National Action Plan (CNAP)

Art Clomera Vice President, Operations On February 9, 2016, the Obama Administration released the Cybersecurity National Action Plan (CNAP), marking the high point of a seven-year effort built upon prior lessons learned from cybersecurity trends, threats, and intrusions. Many experts applauded its comprehensive approach and initiatives to improve federal cybersecurity practices, investing in research, and […]
GRC in Cybersecurity: Why is it Important?

Art Clomera Vice President, Operations Simply put, Governance, Risk, and Compliance (GRC) in cybersecurity fosters a culture of transparency, accountability, and trust by promoting good governance, effective risk management, and regulatory compliance. It originated from the Open Compliance and Ethics Group (OCEG) in 2002 and has become indispensable due to the increasing complexity of cybersecurity […]
What are the NIST Special Publications (SPs) 800 Series?

Art Clomera Vice President, Operations The NIST Special Publication 800 series provides a comprehensive framework for managing the security of federal information systems and the private sector. In federal agencies, these procedural frameworks serve as the very cornerstone of the nation’s cybersecurity, offering guidance to establishing baseline requirements for information security across all agency operations […]
From Risk to Authorization: Understanding ATO in Cybersecurity

Art Clomera Vice President, Operations The Authorization to Operate (ATO) is crucial for the US Federal Government and the Department of Defense (DoD). It represents an official management decision granted by a senior organizational official. The ATO Cybersecurity decision authorizes the operation of an information system and explicitly acknowledges the associated risks to agency operations, […]
Mastering NIST 800-30: A Guide to Effective Risk Assessments

Art Clomera Vice President, Operations In the aftermath of several high-profile breaches and attacks on federal agencies this year, NIST 800-30 helps to translate the intricate vulnerabilities and countermeasures in ways that executive leadership overseeing the agency’s policy implementation can understand. Sharing information enables decision-makers to understand the full extent of the threat landscape in […]
Mastering POA&M Management: Strategies for Effective Continuous Monitoring and Success

Art Clomera Vice President, Operations Plan of Action & Milestones (POA&M) management is the act of compiling a must-do list outlining the actions and milestones needed to address security vulnerabilities and weaknesses within an information system. To this end, a POA&M is a potent management tool because deadlines are assigned for each task, and team […]
Your Shield Against Threats: NIST Security Controls Explained

Art Clomera Vice President, Operations Federal agencies would be paralyzed without the data centers and software systems that store and process data. But many cyberattacks aren’t politically motivated. Government agencies worldwide are often targeted for the vast quantities of personal information they keep about citizens. The market for this stolen data is more lucrative than […]
Key Insights from the NIST AI Risk Management Framework

Art Clomera Vice President, Operations The AI RMF is an extension of the NIST Risk Management Framework (RMF), tailored for artificial intelligence (AI) systems. It provides organizations with a structured approach to identify, assess and manage risks related to AI technologies throughout their lifecycle. The new battlefield is dominated by software and hardware. To navigate […]
Exploring the NIST CSF Categories and Subcategories: A Comprehensive Overview
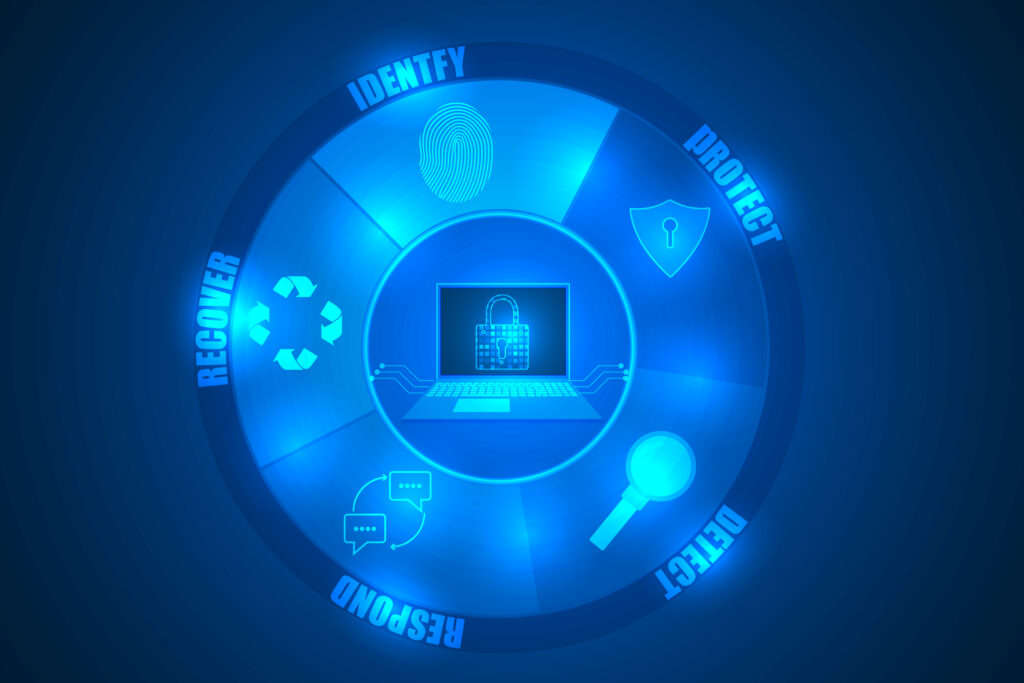
Art Clomera Vice President, Operations Cybersecurity and Infrastructure Security Agency Director Jen Easterly confirmed that a cyberattack on U.S. government networks had affected several Federal agencies. In light of the events when hackers gained access through a security flaw in the widely used file-transfer software, MOVEit Transfer, this article will explore the NIST Cybersecurity Framework […]
Clarifying SSDF: An Overview of the Secure Software Development Framework

Art Clomera Vice President, Operations In response to President Biden’s Executive Order on “Improving the Nation’s Cybersecurity (14028)“, the National Institute of Standards and Technology (NIST) designed the Secure Software Development Framework (SSDF). The creation of the SSDF was a strategic move to bolster the cybersecurity posture of Federal agencies. NIST also developed the Risk […]