Art Clomera
Vice President, Operations
Cybersecurity and Infrastructure Security Agency Director Jen Easterly confirmed that a cyberattack on U.S. government networks had affected several Federal agencies.
In light of the events when hackers gained access through a security flaw in the widely used file-transfer software, MOVEit Transfer, this article will explore the NIST Cybersecurity Framework (CSF).
Some specific applications of the framework include improving an organization’s ability to detect anomalous activity, respond to and recover from incidents as they occur, and identify vulnerabilities, such as the risks associated with file transfer software vulnerabilities.
What are the NIST CSF categories?
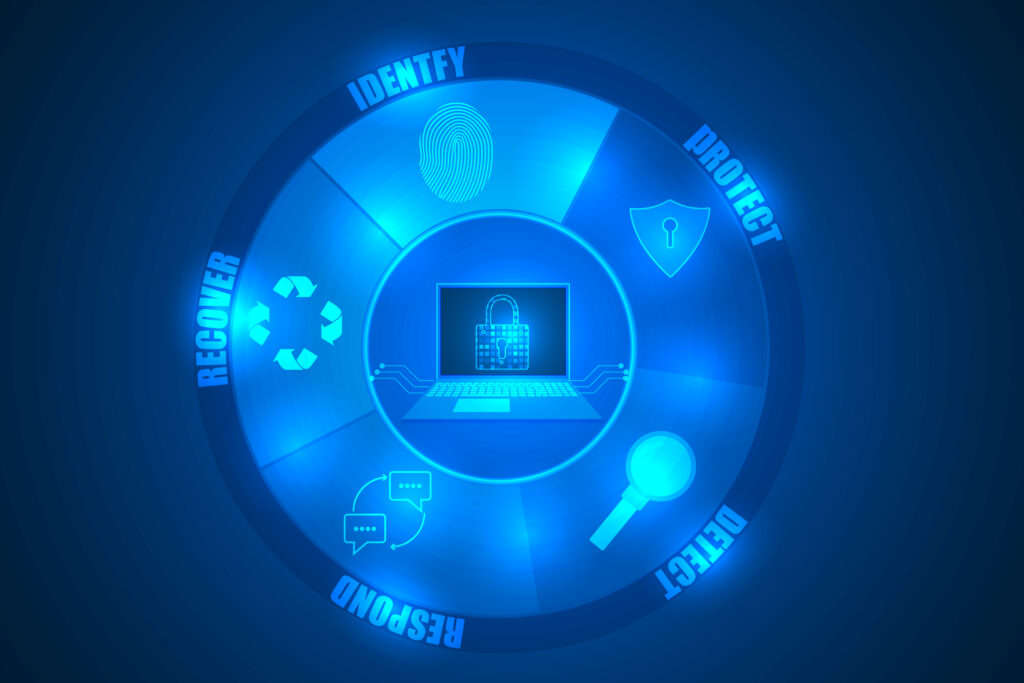
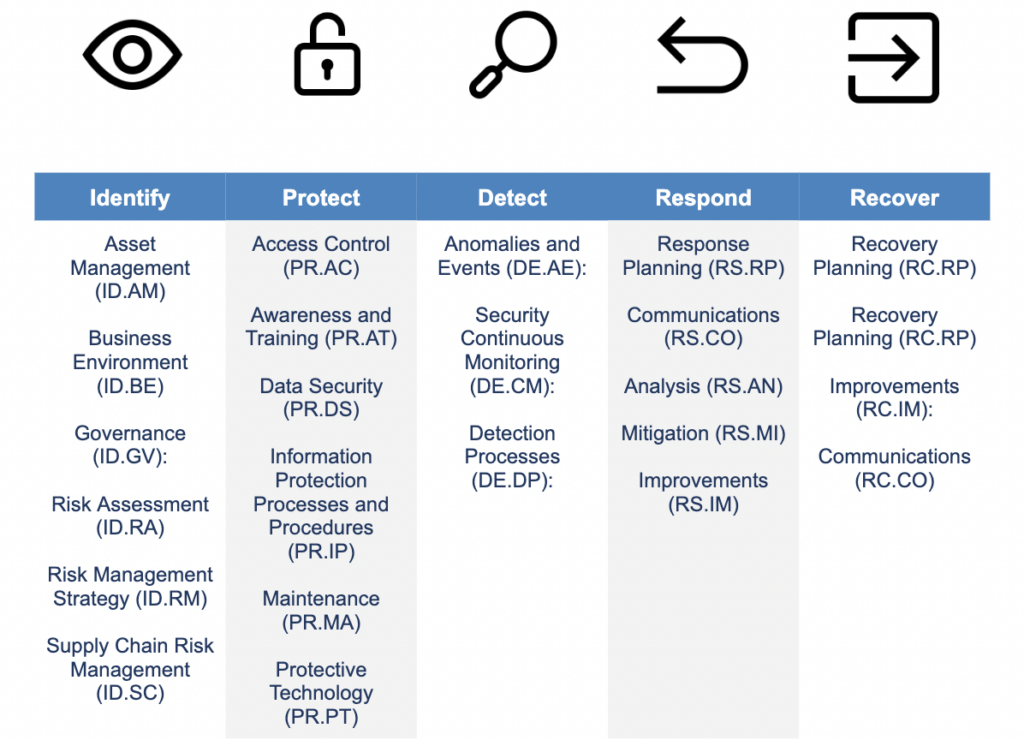
The NIST Cybersecurity Framework (CSF) is divided into three parts: the Framework Core, Profiles, and Tiers. The Framework Core comprises five high-level functions, further broken into 23 NIST CSF categories and 108 NIST CSF subcategories. This structure covers a broad range of cybersecurity objectives while providing more specific guidance on creating robust cybersecurity strategies that civilian and government organizations can use to stay safe.
Identify Categories
Identify is about mapping out a panoramic view of our risk landscapes. By identifying the critical assets, understanding the business environment, establishing governance structures, assessing risks, and formulating a risk management strategy, we can efficiently allocate resources and focus our efforts where they are most needed. This function is valuable in two ways: it enhances cybersecurity posture and optimizes resource utilization.
- Asset Management (ID.AM): Maintain an up-to-date inventory of all devices and software within your organization.
- Business Environment (ID.BE): Understand the organization’s mission, objectives, and cybersecurity risk landscape.
- Governance (ID.GV): Establish and implement policies and procedures that support cybersecurity risk management.
- Risk Assessment (ID.RA): Conduct regular assessments to identify and evaluate cybersecurity risks in your organization.
- Risk Management Strategy (ID.RM): Develop and apply a strategy to manage cybersecurity risks based on your organization’s risk appetite and tolerance levels.
- Supply Chain Risk Management (ID.SC): Identify, assess, and manage the cybersecurity risks associated with your organization’s supply chain and third-party partners.
Protect Categories
Protect helps us limit or contain the potential impact of cybersecurity events by providing six best practice categories. Together they form a shield for an organization, reducing the potential impact of incidents by preventing unauthorized access, safeguarding data, maintaining systems, and educating users about their role in cybersecurity.
- Identify Management and Access Control (PR.AC): Implement robust authorization mechanisms to control sensitive data and systems access.
- Awareness and Training (PR.AT): Develop and maintain a cybersecurity awareness and training program to keep the workforce vigilant.
- Data Security (PR.DS): Establish policies and procedures to protect information at rest and in transit.
- Information Protection Processes and Procedures (PR.IP): Implement security policies for information protection that define roles and responsibilities, manage the lifecycle of information, and protect the integrity of networks.
- Maintenance (PR.MA): Carry out routine preventive maintenance on systems and equipment to ensure their effectiveness and security.
- Protective Technology (PR.PT): Deploy security solutions such as intrusion detection systems, firewalls, and antivirus software to protect your systems and data from cyber threats.
Detect Categories
We can reduce the risk of incidents by detecting potential threats earlier. To this end, the Detect function includes guidance on monitoring various aspects of an organization’s security posture. They help identify deviations from the norm, continuously monitor for signs of threats, and ensure that the processes for detecting these threats are robust and effective.
- Anomalies and Events (DE.AE): Implement systems to detect unusual activity or events that could indicate potential security threats.
- Security Continuous Monitoring (DE.CM): Maintain ongoing awareness of information security, vulnerabilities, and threats to support organizational risk management decisions.
- Detection Processes (DE.DP): Develop and implement processes to ensure cybersecurity events are discovered in time and to support subsequent response and recovery actions.
Respond Categories
Respond is designed to minimize a threat’s impact once detected and regain control. This NIST CSF category is about building an action plan to address detected cybersecurity incidents, including developing and implementing response processes and communications plans. It provides a thorough framework for mitigating the impact of security breaches and restoring system integrity.
- Response Planning (RS.RP): Develop and implement a response plan to handle cybersecurity incidents effectively.
- Communications (RS.CO): Ensure timely and effective communication during and after a security incident, both within the organization and with external stakeholders.
- Analysis (RS.AN): Analyze the impact of a cybersecurity incident to understand its nature and devise appropriate mitigation strategies.
- Mitigation (RS.MI): Take immediate action to contain the impact of a cybersecurity incident and prevent further damage.
- Improvements (RS.IM): Review and learn from cybersecurity incidents to improve response strategies and reduce the likelihood of future occurrences.
Recover Categories
The Recover function emphasizes the importance of timely recovery to normal operations while minimizing the impact of a cybersecurity incident. This category includes restoring systems, learning from the incident, and continuously improving recovery strategies. Its value lies in reducing downtime, managing reputation, and instilling stakeholder confidence.
- Recovery Planning (RC.RP): Establish a recovery plan that ensures a swift return to normal operations.
- Improvements (RC.IM): Learn from incidents and implement improvements to minimize future risks.
- Recovery Planning (RC.RP): Develop and implement a recovery plan to restore systems and operations after a cybersecurity incident.
- Improvements (RC.IM): Incorporate lessons learned from current and past cybersecurity incidents into the recovery strategies to enhance resilience.
- Communications (RC.CO): Establish a communication plan to coordinate with internal teams and external stakeholders during the recovery phase, ensuring transparency and trust.
CSF profile example breakdown
The NIST Cybersecurity Framework (CSF) aims to enhance an organization’s security posture in a targeted and effective way. Its value lies in its flexibility, making it suitable for diverse organizations with specific and unique requirements. Organizations are encouraged to tailor the framework to their circumstances and risk profiles.
This example shows how a CSF profile can be used to establish a roadmap for reducing cybersecurity risk for a large, complex organization. By identifying the specific controls that need to be implemented, tracking the implementation of these controls, and monitoring the effectiveness of the implemented controls, organizations can improve their security posture and reduce their risk of attack.
- Organization: The Department of Defense (DoD).
Risk: The DoD is at risk of a cyberattack, as it operates critical infrastructure and stores sensitive data. - Controls: The CSF profile identifies the following controls that need to be implemented to mitigate the risk of a cyberattack:
- Implement strong identity and access management (IAM) controls. (This control aligns with the “Access Control” category under the “Protect” function.)
- Encrypt all sensitive data. (This control aligns with the “Data Security” category under the “Protect” function.)
- Implement a zero-trust security model. (This control aligns with the “Risk Assessment” category under the “Identify” function.)
- Use continuous monitoring and analysis to detect and respond to threats. (This control aligns with the “Detection Processes” category under the “Detect” function.)
- Implementation: The DoD implements the controls over a time period.
- Monitoring: The DoD monitors the effectiveness of the controls by conducting regular penetration tests and security audits.
- Improvement: The DoD improves its security posture by continuously implementing and improving new controls. (This control aligns with the “Improvement” categories under the “Respond” and “Detect” functions.)
CSF v2.0: What To Expect
NIST CSF was initially developed to protect critical national infrastructure. However, Congress directed NIST to consider the needs of small businesses and higher education institutions when developing v2.0. The update expected in early 2024, will provide additional guidance to organizations on how best to implement the framework to improve their security posture.
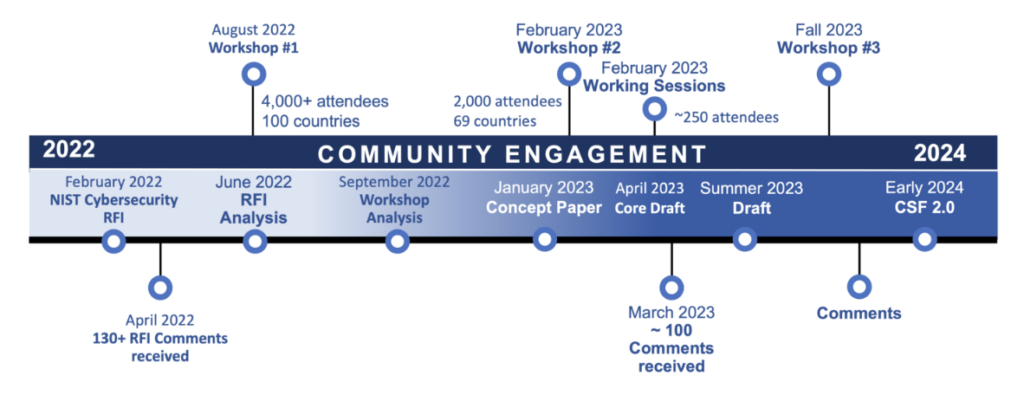
The NIST CSF Timeline. Source
- Supplemental resources: Will provide insight into how the framework can be implemented and measured via theoretical steps that organizations can follow directly or use as reference points.
- Expanded audience: NIST intends the new framework to be more usable by small and medium-sized entities without any potential legal burdens associated with being classified as critical infrastructure.
- Additional resources: NIST plans to expand and update the available resources and documentation provided through the Online Informative Reference Program (OLIR). This will help organizations map security functions across multiple popular frameworks.
Wrapping up
Expanding NIST CSF to include small businesses and higher education institutions is a significant step towards democratizing cybersecurity best practices. This initiative will help organizations map security functions across multiple popular frameworks, further enhancing their ability to effectively implement and align with the CSF. By making the CSF more accessible and applicable to organizations of all sizes, the framework helps strengthen the overall cybersecurity posture and resilience of the entire ecosystem. IPKEYs team of experts stands ready to answer any questions about implementing NIST CSF in your Federal agency.
NIST CSF Categories FAQs
How many NIST categories are there?
There are 23 categories under the NIST Cybersecurity Framework (CSF), divided into five core functions: Identify, Protect, Detect, Respond, and Recover.
How are the NIST CSF categories defined and organized?
The NIST CSF categories are defined and organized within a three-part structure: Functions, Categories, and Subcategories.
- Functions: The five functions of the NIST CSF are:
- Identify: Understand the organization’s assets and the threats and risks to those assets.
- Protect: Implement security controls to protect the organization’s assets.
- Detect: Identify and respond to security incidents.
- Respond: Respond to security incidents to minimize damage.
- Recover: Recover from security incidents to resume normal operations.
- Categories: Each function is divided into several categories, which are specific outcomes of activities related to that function. There are 23 categories in total.
- Subcategories: Each category is further divided into subcategories, which are more specific outcomes of activities related to that category. There are 108 subcategories in total.
What is the purpose of the NIST CSF categories?
The NIST CSF categories provide a structured approach to achieving specific cybersecurity outcomes. They guide organizations in managing and reducing cybersecurity risk by focusing on understanding the business environment, protecting critical infrastructure, detecting potential threats, responding to incidents, and recovering from them.
How can I get started with NIST CSF categories?
To get started with the NIST CSF categories, follow these steps:
- Understand the Framework Implementation Tiers. The Framework Implementation Tiers describe the degree to which an organization’s practices and policies exhibit the traits within the framework. NIST defines four CSF implementation tiers: Partial, Risk-Informed, Repeatable, and Adaptive.
- Determine your implementation tier. Once you understand the Framework Implementation Tiers, you can determine which tier is right for your organization.
- Outline your NIST cybersecurity framework. Once you’ve determined your implementation tier, you can begin outlining your NIST cybersecurity framework by understanding the categories and subcategories that fall under each of the five functions of the Framework Core.
More questions? Chat with our team.