Mastering DFARS Cybersecurity Compliance: Key Requirements & Steps for Success

Explore DFARS compliance, new security measures, and streamlined acquisition pathways to help contractors meet DoD standards.
Adversarial Machine Learning: What NIST’s Latest Report Means for AI Security

Shawn Elliott President, Operations AI systems now shape decisions from grid stability to national security—making them prime targets. Adversaries aim not only to breach systems, but also to manipulate the decision-making process at scale. In response, NIST’s latest report on adversarial machine learning (NIST AI 100-2e2025), finally provides a standardized framework for identifying AI vulnerabilities, […]
Exploring the NIST CSF Categories and Subcategories: A Comprehensive Overview
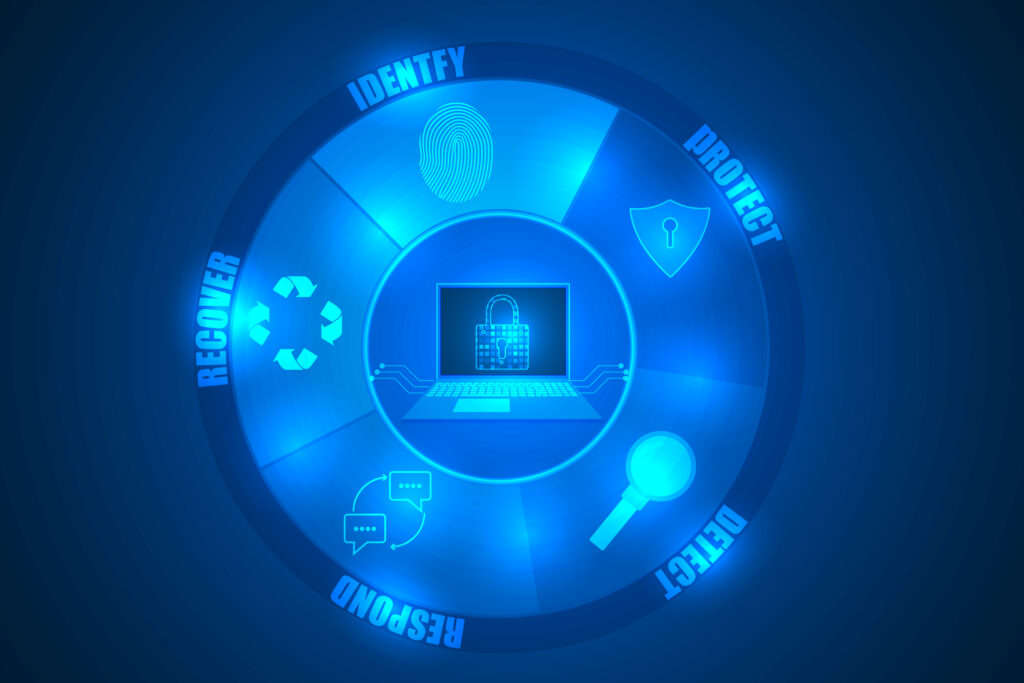
Art Clomera Vice President, Operations Cybersecurity and Infrastructure Security Agency Director Jen Easterly confirmed that a cyberattack on U.S. government networks had affected several Federal agencies. In light of the events when hackers gained access through a security flaw in the widely used file-transfer software, MOVEit Transfer, this article will explore the NIST Cybersecurity Framework […]
The Top GRC Tools and Software for 2026

Art Clomera Vice President, Operations Most organizations succeed (or falter) based on the information they keep and the sophistication with which they can manage it. It’s why having the right GRC tools in place to help manage governance, risk management, and compliance (GRC) issues around information has become a standard organizational strategy. While CISOs […]
Cloud Readiness Assessment: Is Your Organization Ready to Move to the Cloud?

Art Clomera Vice President, Operations The benefits of migrating mission-critical systems and data to the cloud are many and well-documented: agility, access to cutting-edge technology, cost savings, efficiency, scalability, and resilience. But before diving headfirst, how do you know if your organization is ready for the transition? Enter the cloud readiness assessment. The Cloud […]
Elevating Efficiency with RPA: Five Real-World RPA Examples

How did IPKeys develop and deploy over 100 RPA use cases across the Defense Logistics Agency’s (DLA) departments? How did we contribute +130,000 mission hours to DLA with Robotic Process Automation? How did we help the DLA achieve unattended automation architecture? Looking for RPA examples and process steps? We’re revealing our blueprint.
Demystifying Software Bill of Materials (SBOM): A Comprehensive Guide

Art Clomera Vice President, Operations It’s hard to believe that until recently, organizations lacked a reliable method to know what components were in their software – imagine opening a medicine bottle and not finding the ingredients label. While the Software Bill of Materials (SBOM) has been around for a decade, it’s gained traction in the […]
GRC in Cybersecurity: Why is it Important?

Art Clomera Vice President, Operations Simply put, Governance, Risk, and Compliance (GRC) in cybersecurity fosters a culture of transparency, accountability, and trust by promoting good governance, effective risk management, and regulatory compliance. It originated from the Open Compliance and Ethics Group (OCEG) in 2002 and has become indispensable due to the increasing complexity of cybersecurity […]
Mastering POA&M Management: Strategies for Effective Continuous Monitoring and Success

Art Clomera Vice President, Operations Plan of Action & Milestones (POA&M) management is the act of compiling a must-do list outlining the actions and milestones needed to address security vulnerabilities and weaknesses within an information system. To this end, a POA&M is a potent management tool because deadlines are assigned for each task, and team […]
Risk Management Framework (RMF): The Complete Guide for 2026

Art Clomera, Vice President, Operations Every organization has to manage risk in one form or another. Suppliers manage the risk of having too much or too little product in stock, legal risks are present in virtually every contract negotiation, and of course, insurance companies are built entirely on the principle of managing risk for their […]