
Art Clomera
Vice President, Operations
2026’s cybersecurity landscape demands a new breed of cybersecurity tools, ones that blend cutting-edge technology with predictive intelligence, advanced analytics, and adaptive strategies. Deep learning algorithms and comprehensive data analysis empower these tools to be proactive and predictive, seamlessly integrating into cloud, on-premises, and hybrid environments.
This year’s challenges are formidable. We face increased AI use in offensive and defensive cyber operations, persistent back-office software targeting, and the ever-present threat of ransomware and advanced persistent threats.
To overcome these challenges, collaboration is key. Sharing threat intelligence and best practices within our professional communities is crucial. While, for federal agencies, the fight demands strategic investment in top-tier cybersecurity tools and technologies tailored to their unique needs, resources, and budgets.
Next, let’s delve deeper into why these tools are vital in today’s digital battlefield.
What are cybersecurity tools?
Cybersecurity tools are applications or software designed to protect your systems, data, and networks from unauthorized access, attacks, and breaches.
Without them, the confidentiality and integrity of the spectrum of data, ranging from personal information to digital transactions to classified information, lie at the mercy of bad actors.
These tools range from antivirus software and firewalls to more advanced solutions like intrusion detection systems, encryption tools, and cybersecurity analytics platforms. As we’ll see in a moment, no cybersecurity tool can do it all – the landscape is simply too complex for that.
No Solution Can Do It All: A Guide to the Different Cybersecurity Tools of 2026
Cybersecurity in 2026 faces a vastly different landscape compared to the past. Once considered reliable defenders, simple firewalls and antivirus solutions can no longer effectively guard against today’s threats. The digital terrain has transformed into a complex ocean of interconnected devices, cloud networks, and vast amounts of data, creating a fertile ground for intricate and unpredictable cyberattacks.
The potential entry points for malicious actors (attack surfaces) expand into multi-domain environments that traditional security measures struggle to secure fully. This necessitates a significant shift in our approach, demanding sophisticated technologies, adaptable strategies, and a deeper understanding of the ever-evolving threat landscape.
A breakdown of the best cybersecurity tools for 2026
Cybersecurity tools offer a variety of IT defenses. The right tool addresses your specific vulnerabilities and risk profile to ensure they integrate seamlessly to provide a holistic view of your security posture. It may or may not include an open-source option that is cost-effective in the short term but may incur additional expenses in the long term due to the expertise required for management.
So, study your risk profile, analyze your vulnerabilities, and select your digital tools wisely. Remember, cybersecurity is not a sprint. It’s a marathon.
| # | Tool / Category | Example | Primary Use |
|---|---|---|---|
| 1 | Cybersecurity analytics & RMF automation | IPKeys CLaaS® | Unified AI-driven analytics, POA&M automation |
| 2 | Enterprise cyber risk & compliance | Xacta.io (Telos) | Automated control selection, continuous compliance |
| 3 | Password management | Keeper Security | Enterprise password vaulting & governance |
| 4 | CASB / DLP endpoint security | McAfee MVISION Cloud | Threat prevention, DLP, identity & encryption |
| 5 | Packet sniffer / network analyzer | Wireshark | Deep packet inspection & traffic troubleshooting |
| 6 | SIEM | Fortinet SIEM | Real-time analytics, correlation, UEBA |
| 7 | Endpoint & workload protection | VMware Carbon Black Cloud | Prevent/detect/respond to malware & ransomware |
| 8 | Intrusion detection / prevention (IDS/IPS) | Snort | Rule-based real-time traffic analysis |
| 9 | Free gov resources aligned to NIST CSF | CISA Services & Tools | Assessments, scanners, guidance |
1. Best for federal agencies: IPKeys Cyber-Lab-as-a-Service
IPKeys has a strong track record of delivering successful projects for federal agencies, focusing on providing exceptional technical expertise, DoD-inspired technologies, and leading-edge solutions.
IPKeys Cyber-Lab-as-a-Service (CLaaS) is a cloud-based cybersecurity solution designed for federal agencies. The platform offers features and benefits, making it an ideal choice for federal agencies looking to enhance their cybersecurity posture.
It excels as a unified, AI-fueled RMF automation analytics and reporting platform optimized for federal agencies. Fully configurable, this next-gen platform is tailored to the specific needs of federal agencies, allowing them to identify, calculate, and quantify security risks.
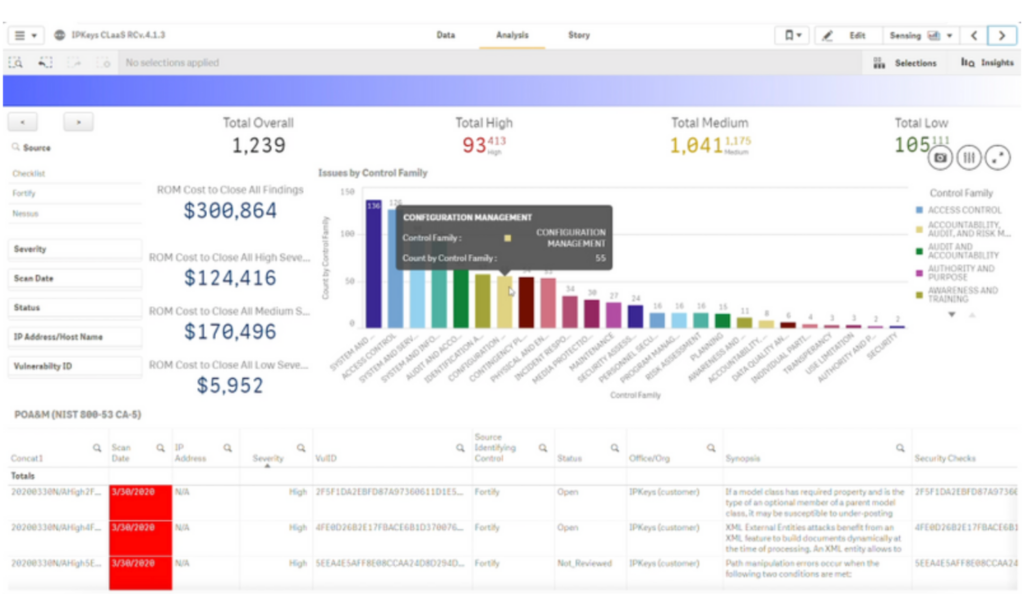
Key features and benefits
- More than just reporting: CLaaS takes actionable steps to mitigate vulnerabilities and automates the generation of Plan of Actions and Milestones (POA&Ms)
- Advanced threat detection: The platform utilizes cutting-edge algorithms to unmask hidden threats lurking in your network traffic’s shadows. No suspicious login attempt, malware-laden data packet, or malicious script can escape its watchful gaze
- Customizable alerts and reporting: Set optimal thresholds for your agency, allowing you to balance workload with threat levels
- Real-time network behavior analysis: Beyond individual events, ClaaS deciphers the subtle shifts and anomalies that reveal the true story behind the data
- Meet federal requirements quickly: Stay ahead of compliance mandates like OMB Memo M-19-19 and Federal Cloud Smart and stringent standards like FedRAMP, FISMA, and NIST through automated RMF assessments, policy enforcement, and continuous monitoring
- Actionable insights, not data deluge: We’ve all been there, drowning in SIEM alerts and endless logs. ClaaS provides straightforward, actionable insights, highlighting what truly matters
- Scalability: Your network grows, and your threats evolve. ClaaS adapts and scales to meet your needs, whether you’re a small, medium, or large agency
2. Best for enterprise companies: Xacta.io

Developed by Telos Corporation, Xacta.io is a comprehensive cyber risk management platform that addresses the complex challenges of automated control selection, assessment, and continuous compliance monitoring.
Xacta.io analyzes your unique enterprise environment and automatically recommends the most relevant security controls to implement, saving time and resources compared to manual assessment.
It goes beyond traditional vulnerability scanning, evaluating the effectiveness of your current controls and pinpointing potential shortcomings.

Key features and benefits
- Automated control selection: Helps organizations to identify and prioritize controls based on their specific needs and requirements
- Continuous compliance monitoring: Identify and address compliance issues in real-time
- Risk assessment: Organizations can prioritize and identify risks based on how likely they are to occur and their potential impact
- Compliance: Aggregates scan results from multiple security products, mapping them to controls like NIST 800-53 and FedRAMP for continuous compliance and trend analysis
- Workflow automation: These capabilities streamline the compliance process and reduce the risk of human error
- Real-time visibility: For quick identification and resolution of compliance issues
3. Best for password management: Keeper Security

Trusted by millions of individuals and organizations globally, Keeper is the leader in best-in-class password and passkey management, secrets management, privileged access, secure remote access, and encrypted messaging.
Weak passwords are the gateway to data breaches, but managing them for an entire organization in today’s complex IT landscape can be arduous. That’s where Keeper Security steps in, offering a robust and feature-rich password management solution tailored to the needs of enterprises.

Key features and benefits
- Secure Password Storage and Sharing: Keeper provides an encrypted platform for storing and sharing passwords securely
- Dark Web Monitoring: Proactively monitors and alerts users about their credentials being compromised on the dark web
- Zero-Knowledge Security Architecture: Only the user can access their encrypted data
- Strong Encryption and Multi-Factor Authentication: Utilizes 256-bit AES encryption and options like Touch ID for heightened security
- Enterprise Password Management (EPM): Provides organizations with complete visibility and control over password practices.
- Continuous Software Updates: Regular updates ensure access to the latest cybersecurity solutions.
4. Best for DLP endpoint security: McAfee MVision Cloud

McAfee acquired Skyhigh Networks in 2018 and integrated its cloud security capabilities into the MVISION Cloud platform.
Federal agencies can also take advantage of the DoD Antivirus Software License Agreement with McAfee, which allows active DoD employees and authorized government contractors to utilize the antivirus software for personal use.
This subscription provides proactive security that can prevent malicious attacks and keep users safe while browsing, searching, and downloading files online.

Key features and benefits
- Threat Prevention: MVISION Cloud includes advanced threat prevention, device security, and email protection
- Data Loss Prevention (DLP): The platform provides data loss prevention capabilities, ensuring that critical data stays secure within the company, fostering a sense of reliability
- Incident Response: These features allow organizations to respond effectively to security incidents and data breaches
- Identity Management and Encryption: The Premium version of MVISION Cloud includes identity management, encryption, governance, and visibility and control over SaaS operations, providing comprehensive security and compliance capabilities
- FedRAMP Authorization: It’s the first Cloud Access Security Broker (CASB) platform authorized by the FedRAMP program’s Joint Authorization Board (JAB). Ten federal agencies, including NASA and the FDA, are utilizing the system.
Bonus for federal agency remote workers
McAfee’s Work From Home (WFH) initiative allows individuals to download top-tier antivirus and secure Virtual Private Network (VPN) solutions. This program is designed to bolster system protection in light of the heightened mission need to support telework requirements. Click here for more.
5. Best Packet Sniffer: Wireshark

Wireshark is a highly acclaimed, free, open-source network protocol analyzer widely used by IT professionals and cybersecurity experts worldwide. Its primary function is to capture and display network data as it flows in real time – making it an essential tool for network troubleshooting, analysis, and education.
While Wireshark might not be the most user-friendly tool for beginners, its vast capabilities and open-source nature make it an invaluable asset for anyone who wants to understand and secure their network.
The cybersecurity tool burrows deep into the data packets, peeling away layers to reveal everything from protocols and headers to actual payload content. This granular view lets you identify anomalies, troubleshoot network issues, and uncover malicious activity hidden within seemingly innocuous packets.

Key features and benefits
- Deep Packet Inspection: Wireshark captures and analyzes the data packets that travel across a network and provides detailed insights into network traffic, helping users identify and resolve complex network issues
- Broad Protocol Support: It’s compatible with a wide range of network protocols, enhancing its versatility in analyzing various kinds of network traffic
- Real-time packet capturing: Enables immediate analysis of network issues as they occur
- Graphical User Interface (GUI): Despite being a powerful tool, Wireshark’s GUI is user-friendly, making it accessible to beginners and advanced users
- Filtering and Search Capabilities: Users can filter and search for specific packets, which is invaluable in isolating problematic network traffic or specific security threats
- Export and Reporting Functions: The ability to export data in various formats and generate detailed reports enhances its utility for network analysis and troubleshooting
6. Best for SIEM: Fortinet SIEM

Many SIEM solutions will give you similar abilities. However, the odds are that just one SIEM will perfectly fit your needs. Are you interested in NOC capabilities (device monitoring) or security logs? Will you send flows to the SIEM? How many people are on your security team? How many servers/networks/devices will be monitored?
Fortinet’s SIEM solution offers advanced threat detection using analytics and threat intelligence, which is crucial for identifying security incidents like APTs in federal agencies.
It’s designed for compliance management and supports standards like FedRAMP, FISMA, and NIST, which are essential for federal operations.

Key features and benefits
- Self-learning asset inventory: Passive & active discovery methods, use of agents, FortiGates, & OT asset management systems
- Real-time security analytics: Correlation, UEBA ML engine, and over 1600 rules provide robust threat detection
- Powered by generative AI: To guide, simplify, and automate security analyst activities
- OSQUERY endpoint visibility: Seamless integration provides extended endpoint investigation and forensic monitoring
- Deep fabric integration: Integration with third-party solutions via robust APIs
- Industry-leading threat intelligence: Driven by over 500 researchers and AI fed by the world’s most extensive array of sensors
7. Best for Endpoint and Workload Protection: VMware

VMware Carbon Black Cloud is a cloud-native endpoint and workload protection platform that has received FedRAMP authorization. It offers comprehensive malware protection using advanced behavioral analytics and threat intelligence.
The platform is designed to adapt to unique environments and threat landscapes, providing effective endpoint protection that combines prevention and automated detection to defend against advanced cyber-attacks.

Key features and benefits
- Endpoint Protection: Advanced capabilities to prevent, detect, and respond to cyber attacks, including malware and ransomware
- Behavioral Analytics: Detect abnormal activities and potential threats based on deviations from standard network behaviors
- Threat Intelligence (TI): Ensures the system knows the latest cyber threats and vulnerabilities
- Cloud-Native Architecture: Offers scalability and flexibility, allowing the platform to adapt to an organization’s changing needs and size easily
- Automated Response and Remediation: Reduces the need for manual intervention and speeding up the resolution process
8. Best for Threat Detection: Snort

With over 5 million downloads, Snort is the world’s most widely deployed intrusion prevention system (IDS). Being open-source and community-supported, Snort benefits from frequent updates and a large user base contributing rules and support. It’s compatible with operating systems like UNIX, Linux, and Windows.
Snort isn’t a one-size-fits-all solution. It requires some configuration and understanding of its rule-based system. However, for those willing to invest the effort, Snort allows you to write your own rules, tailoring them to your specific network environment and security needs. This flexibility lets you focus on the threats that matter most, adding layers of protection against targeted attacks and emerging vulnerabilities.

Key features and benefits
- Real-time traffic analysis: Identify a range of attacks and probes, including buffer overflows and stealth port scans
- Protocol analysis and content searching: Scrutinize network packets to identify indicators of malicious traffic.
- Customizable rule-based detection system: Users can write their own rules or modify existing community-provided ones
- Detailed network traffic data: For analysis and troubleshooting
- Integrate with other security tools: Like SIEM systems, for comprehensive network security management
- Alerting and logging options: Including file logging, SNMP traps, and desktop pop-up windows
9. Free Cybersecurity Services and Tools Aligned with NIST Framework: CISA
CISA provides free cybersecurity services and tools aligned with the NIST Cybersecurity Framework to enhance security in critical infrastructure and government entities. To access these resources, visit CISA’s Free Cybersecurity Services and Tools.

Need help deciding? Look for these eight features in a cybersecurity tool
More than any other organization, federal agencies need tools capable of detecting a broad spectrum of threats, including known malware, zero-day attacks, phishing, ransomware, zero-day attacks, and advanced persistent threats (APTs).
1. Scalability and performance for complex networks
Federal networks are not static; they are continually evolving and expanding, necessitating tools that can adapt and scale without difficulty. The ideal cybersecurity tool should be capable of scaling up as the network grows without requiring extensive modifications or overhauls. This scalability is vital to accommodate the increasing number of users, higher data volumes, and more complex network architectures that federal agencies typically experience.
Alongside scalability, performance is a crucial factor. The tool should maintain a consistent level of performance, even as the network scales. The tool should function efficiently, managing large datasets and high traffic volumes without lag or downtime, ensuring uninterrupted network operations.
Lastly, the right tool should integrate seamlessly with the current network infrastructure, operating in a way that does not hinder or slow down regular network functions and user activities.
2. Open ecosystem and integrations
Drowning in a sea of standalone security tools, each fighting their own siloed battles? An open ecosystem throws you a lifeline. Connect your tools, unleash their combined intelligence, and simplify your security architecture.
Utilizing open APIs, connectors, and automation scripts enables organizations to enhance the utility of their existing products and lower costs. This is achieved by simplifying the architecture and deployment processes of the increasingly complex array of cybersecurity solutions.
3. FedRAMP-authorized with robust vulnerability management
FedRAMP authorization is a testament to a tool’s compliance with high-security standards set by the federal government. It indicates that the tool has undergone rigorous assessments and meets the comprehensive security requirements for handling sensitive federal data. This authorization is especially important for tools deployed in cloud environments, ensuring they provide the necessary security controls to protect federal information.
Ensure your chosen tool adheres to FedRAMP High Baselines for maximum security compliance. And look for capabilities like automated vulnerability scanning, prioritization based on risk levels and federal regulations, and patching tools aligned with DISA STIGs (Security Technical Implementation Guides).
4. Advanced threat detection and prevention
Advanced tools don’t just raise an alarm when a threat is detected. They take immediate action. They can quarantine infected systems, block malicious traffic, and automatically remediate affected areas, minimizing damage and downtime.
Look for the following features:
- Multi-layered Defense: Advanced tools go beyond simple signature-based detection, employing machine learning, behavioral analysis, and sandboxing to identify and neutralize even the most cunning zero-day threats and targeted attacks.
- Uncovering Hidden Threats: They delve deeper into your network, analyzing seemingly innocuous activity and anomalies to expose hidden malware, insider threats, and compromised systems before they escalate.
- Predictive Intelligence: They leverage threat intelligence feeds and real-time data analysis to predict potential attack vectors and strengthen defenses before threats materialize.
5. Integrated vulnerability management and remediation
Every system has vulnerabilities — integrated tools proactively scan your entire IT infrastructure—networks, devices, applications, and operating systems—to uncover these potential weaknesses and vulnerabilities before they’re exploited.
Integrated tools also streamline workflows, enabling action by consolidating vulnerability data and remediation tasks into a single, unified dashboard, providing a clear view of your security posture and simplifying management.
They also align remediation efforts with your organization’s specific risk tolerance and business objectives, ensuring a strategic and cost-effective approach to vulnerability management.
6. Threat Intelligence (TI) and continuous monitoring
Stay in front of emerging threats with access to real-time threat feeds and continuous vulnerability monitoring. Look for tools that track attacker tactics, techniques, and procedures (TTPs) relevant to federal agencies and provide actionable insights for proactive defense.
Prioritize solutions that use AI and machine learning for proactive threat detection and protection across all attack vectors relevant to federal operations. This includes endpoints, networks, cloud services, and email systems.
7. Real-time monitoring and alerts
Consider the following to ensure the system can deliver instant alerts for potential threats, enabling rapid response to minimize security incident impacts.
Look for alert mechanisms that can be tailored to the agency’s specific needs, helping to distinguish critical alerts from false positives.
Select tools with advanced filtering capabilities to differentiate real threats from routine anomalies, reducing manual oversight and preventing alert fatigue. Also, choose systems that prioritize alerts based on threat severity, allowing security teams to focus on the most pressing issues first for an effective response.
8. Robust vulnerability management for federal compliance
Federal IT leaders face significant security challenges, with a report by the Ponemon Institute revealing that over half of federal IT and cybersecurity professionals have experienced cybersecurity incidents causing substantial disruptions to their operations. These leaders must tackle threats from various angles, including some of the world’s most sophisticated and relentless cyber threats.
Tools should support compliance with FISMA (the Federal Information Security Management Act), NIST (National Institute of Standards and Technology) guidelines, and CISA (Cybersecurity and Infrastructure Security Agency) guidelines. This ensures that the tools help identify and manage vulnerabilities within the system and align with the specific requirements set by federal cybersecurity mandates.
Additional features for federal cybersecurity tools
- User-Friendly Design: Ensure tools are accessible to personnel with varying levels of cybersecurity expertise
- Scalability: Select solutions scalable to evolving federal agency needs and technological advancements
- Integration Capabilities: Focus on tools that integrate well with existing federal IT and security systems
- Cost-Effectiveness: Evaluate the tool’s cost relative to the value and security it provides, considering federal budget constraints
Wrapping up
Federal agencies can build a multi-layered defense that safeguards sensitive data and operations by focusing on key features like FedRAMP-authorized tools, robust vulnerability management aligned with NIST and CISA guidelines, and advanced threat detection capabilities.
In addition to IPKeys ClaaS, we offer cybersecurity services and tools tailored to federal agencies to enhance cybersecurity programs and combat modern threats.
- Cybersecurity Threat Monitoring, Assessment, and Defense
- Risk Assessments and Network Resiliency Ratings
- Risk Management Framework (RMF) Transitions
- Configuration Management
- Security Tools Implementation and Management
Please contact our team for more information or to receive expert help with FedRAMP compliance and integrating security tools in government settings.
Cybersecurity tools – common FAQs
Why is having a cybersecurity program important?
With our increasing dependence on technology, cyber attacks’ potential impact and risks are escalating. For instance, a cyber attack can incapacitate a hospital’s operations, cause a power grid failure, or, in extreme cases, trigger a conflict.
Having a solid cybersecurity program in place can help organizations:
- Protect sensitive data and systems by thwarting cybercriminals from stealing data, disrupting operations, or demanding ransoms
- Maintain compliance with regulations by meeting industry and government data security and privacy protection standards
- Preserve the organization’s reputation and trust by averting reputational damage that can erode trust and costly data breaches
How long does integrating with a cybersecurity tool and setting up a program take?
Integration time varies. Depending on the complexity of the tool, existing infrastructure, and organizational readiness, it typically requires anything from 1-3 months for smaller businesses up to 6-12 months for larger enterprises.
Multiple factors can influence these timelines, including the IT environment’s complexity, the organization’s size, program scope, and available resources.
How much does cybersecurity software cost?
Prices vary widely depending on features, number of users, deployment model (on-premise vs. cloud-based), and vendor pricing structures.
Typical price ranges per month include:
- Small businesses $50-$500
- Mid-sized organizations $500-$5,000
- Large enterprises $5,000+
- Most vendors provide tailored pricing based on specific needs



